参考博文:【Nginx的SSL配置优化】https://www.linpx.com/p/ssl-configuration-optimization.html
一、SSL Labs
ssllabs:查看https网站的安全级别: https://www.ssllabs.com/ssltest/index.html
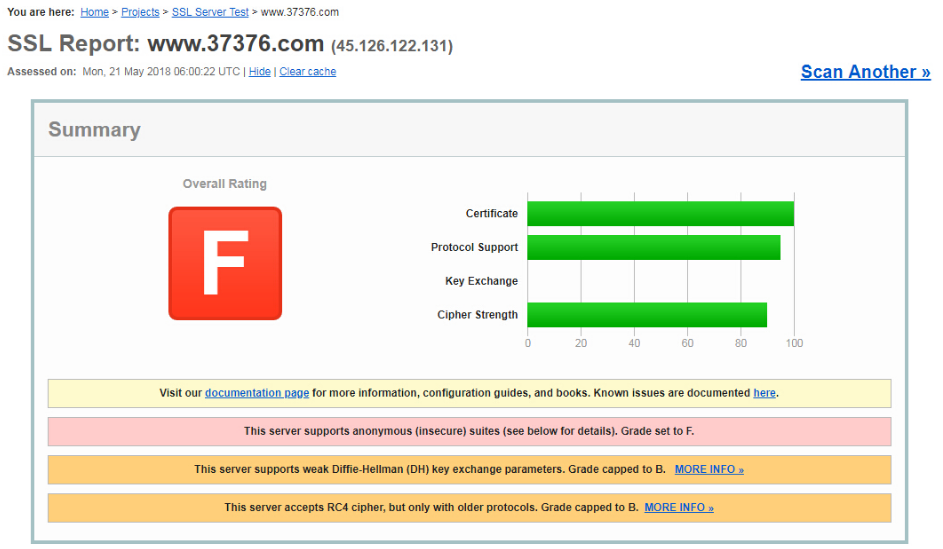
未加入ssl优化配置的安全级别F
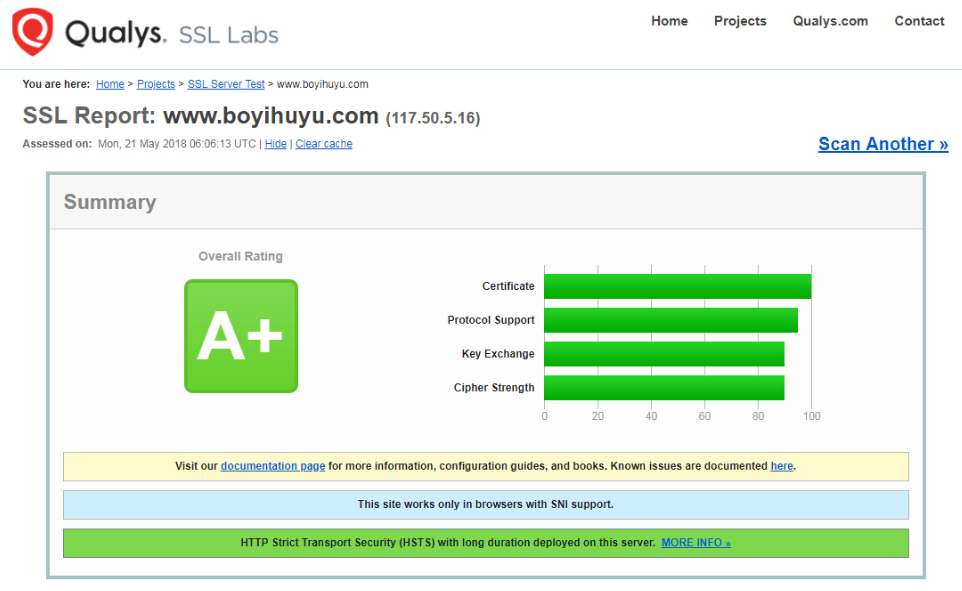
配置了ssl优化参数的安全级别A+
二、创建dhparam nginx.pem秘钥
- 一般网站使用的SSL证书都是RSA证书,这种证书基本都是2048位的密钥,但是证书密钥交换密钥必须要比证书密钥更长才能安全。
- 而默认的创建dhparam.pem只有1024位,所以我们需要手动生成一个更强的密钥4096位。
1
2
3
4
| # 执行时间很长,建议使用screen生成
mkdir -p /usr/local/nginx/ssl-key/dh_ssl
cd /usr/local/nginx/ssl-key/dh_ssl
openssl dhparam -out nginx.pem 4096
|
三、ssl配置及优化
配置如下,只包含ssl部分的配置,未包含其他比较重要的配置,如缓存、跳转、防盗链和强制HTTPS等等。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
| upstream www.test.com_ssl {
server 127.0.0.1 weight=20 max_fails=2 fail_timeout=8s;
}
server
{
listen 443 ssl;
server_name www.test.com;
# SSL base
ssl on;
ssl_certificate /usr/local/nginx/ssl-key/STAR.test.com/STAR.test.com.crt;
ssl_certificate_key /usr/local/nginx/ssl-key/STAR.test.com/STAR.test.com.key;
ssl_dhparam /usr/local/nginx/ssl-key/dh_ssl/nginx.pem;
ssl_session_timeout 1d;
ssl_session_cache shared:SSL:50m;
ssl_session_tickets on;
# SSL ciphers
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers 'ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES256-SHA:ECDHE-ECDSA-DES-CBC3-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:DES-CBC3-SHA:!DSS';
ssl_prefer_server_ciphers on;
# OCSP Stapling
#ssl_trusted_certificate /usr/local/nginx/ssl-key/GlobalSign/chain.pem;
#ssl_stapling on;
#ssl_stapling_verify on;
#resolver 8.8.8.8 8.8.4.4 valid=300s;
#resolver 119.29.29.29 223.5.5.5 valid=300s;
#resolver_timeout 5s;
# HSTS
add_header Strict-Transport-Security max-age=15768000;
#add_header X-Frame-Options DENY;
#add_header X-Content-Type-Options nosniff;
location / {
proxy_redirect off;
proxy_pass http://www.test.com_ssl;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header REMOTE-HOST $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_next_upstream timeout invalid_header http_500 http_502 http_503 http_504; # http_404;
}
client_max_body_size 100m;
client_body_buffer_size 128k;
proxy_connect_timeout 90;
proxy_read_timeout 90;
proxy_send_timeout 90;
proxy_buffer_size 64k;
proxy_buffers 32 32k;
proxy_busy_buffers_size 128k;
proxy_temp_file_write_size 64k;
large_client_header_buffers 4 16k;
error_log /data/httplogs/www.test.com-ssl-error.log;
access_log /data/httplogs/www.test.com-ssl-access.log weblog;
}
|
配置解析
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
| server {
listen 443 ssl;
# listen 443 ssl http2;
# 使用HTTP/2,需要Nginx1.9.7以上版本
server_name www.test.com;
# SSL base ssl基础配置区块,SSL证书文件位置
ssl on;
ssl_certificate /usr/local/nginx/ssl-key/STAR.test.com/STAR.test.com.crt;
# https证书,其实是个公钥,它会被发送到连接服务器的每个客户端
ssl_certificate_key /usr/local/nginx/ssl-key/STAR.test.com/STAR.test.com.key;
# 证书私钥是用来解密的,所以它的权限要得到保护。让nginx的主进程能够读取。当然私钥和证书可以放在一个证书文件中,这种方式也只有公钥证书才发送到client
# SSL ciphers 加密算法及交换秘钥配置区块
ssl_dhparam /usr/local/nginx/ssl-key/dh_ssl/nginx.pem;
# DH-Key交换密钥文件位置
ssl_ciphers 'ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES256-SHA:ECDHE-ECDSA-DES-CBC3-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:DES-CBC3-SHA:!DSS';
# 选择加密套件,不同的浏览器所支持的套件(和顺序)可能会不同。这里指定的是OpenSSL库能够识别的写法,你可以通过 openssl -v cipher 'RC4:HIGH:!aNULL:!MD5'(后面是你所指定的套件加密算法) 来看所支持算法。
ssl_prefer_server_ciphers on;
#由服务器协商最佳的加密算法
# OCSP Stapling OCSP配置区块
ssl_trusted_certificate /usr/local/nginx/ssl-key/GlobalSign/chain.pem;
# OCSP Stapling的证书位置
ssl_stapling on;
# OCSP Stapling开启,OCSP是用于在线查询证书吊销情况的服务,使用OCSP Stapling能将证书有效状态的信息缓存到服务器,提高TLS握手速度
ssl_stapling_verify on;
# OCSP Stapling验证开启
#resolver 8.8.8.8 8.8.4.4 valid=300s; # 海外dns(美国)
resolver 119.29.29.29 223.5.5.5 valid=300s; # 国内dns(腾讯和阿里)
# 用于查询OCSP服务器的DNS
resolver_timeout 5s;
# 查询域名超时时间
# HSTS 配置区块
add_header Strict-Transport-Security max-age=10886400;
# 开启HSTS,并设置有效期为“10886400秒”(最低不低于18周)
# add_header Strict-Transport-Security "max-age=6307200; includeSubdomains; preload";
#开启HSTS,并设置有效期为“6307200秒”(6个月),包括子域名(根据情况可删掉),预加载到浏览器缓存(根据情况可删掉)
add_header X-Frame-Options DENY;
# 禁止被嵌入框架
add_header X-Content-Type-Options nosniff;
# 防止在IE9、Chrome和Safari中的MIME类型混淆攻击
# SSL optimize ssl优化配置区块
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
# 指令用于启动特定的加密协议,nginx在1.1.13和1.0.12版本后默认是ssl_protocols SSLv3 TLSv1 TLSv1.1 TLSv1.2,TLSv1.1与TLSv1.2要确保OpenSSL >= 1.0.1 ,SSLv3 现在还有很多地方在用但有不少被攻击的漏洞。
ssl_session_cache shared:SSL:50m;
# Session Cache,将Session缓存到服务器,这可能会占用更多的服务器资源
# ssl_session_cache builtin:1000 shared:SSL:10m;
# 设置ssl/tls会话缓存的类型和大小。如果设置了这个参数一般是shared,buildin可能会参数内存碎片,默认是none,和off差不多,停用缓存。如shared:SSL:10m表示我所有的nginx工作进程共享ssl会话缓存,官网介绍说1M可以存放约4000个sessions。
ssl_session_tickets on;
# 开启浏览器的Session Ticket缓存
ssl_session_timeout 1d;
# SSL session过期时间,系统默认5分钟太短了,可以设成30m即30分钟甚至4h
……
}
|
ssl_ciphers加密套件配置
ssl_ciphers加密套件配置可以直接通过这个链接来查看。
https://mozilla.github.io/server-side-tls/ssl-config-generator/




